RADIUS accounting is a critical component of the RADIUS protocol that collects data for statistical purposes, network monitoring, and accurate billing of users. This process works alongside RADIUS authentication and authorisation to create a comprehensive network security solution.
The complete RADIUS accounting process
The RADIUS accounting process begins when a user is granted access to the RADIUS server. This process tracks all aspects of user access to the network and creates a detailed record of network resource usage.
Step 1: Accounting Start
Once the user has been granted access to the RADIUS server, the Network Access Server (NAS) sends a RADIUS Accounting Request packet to the RADIUS server. This packet, known as an Accounting Start, signifies that the user’s access to the network has begun.
The Accounting Start packet typically contains:
- Username and password verification status
- User information and network address
- Point of access (such as wireless access points)
- A unique session identifier
- Timestamp of when access began
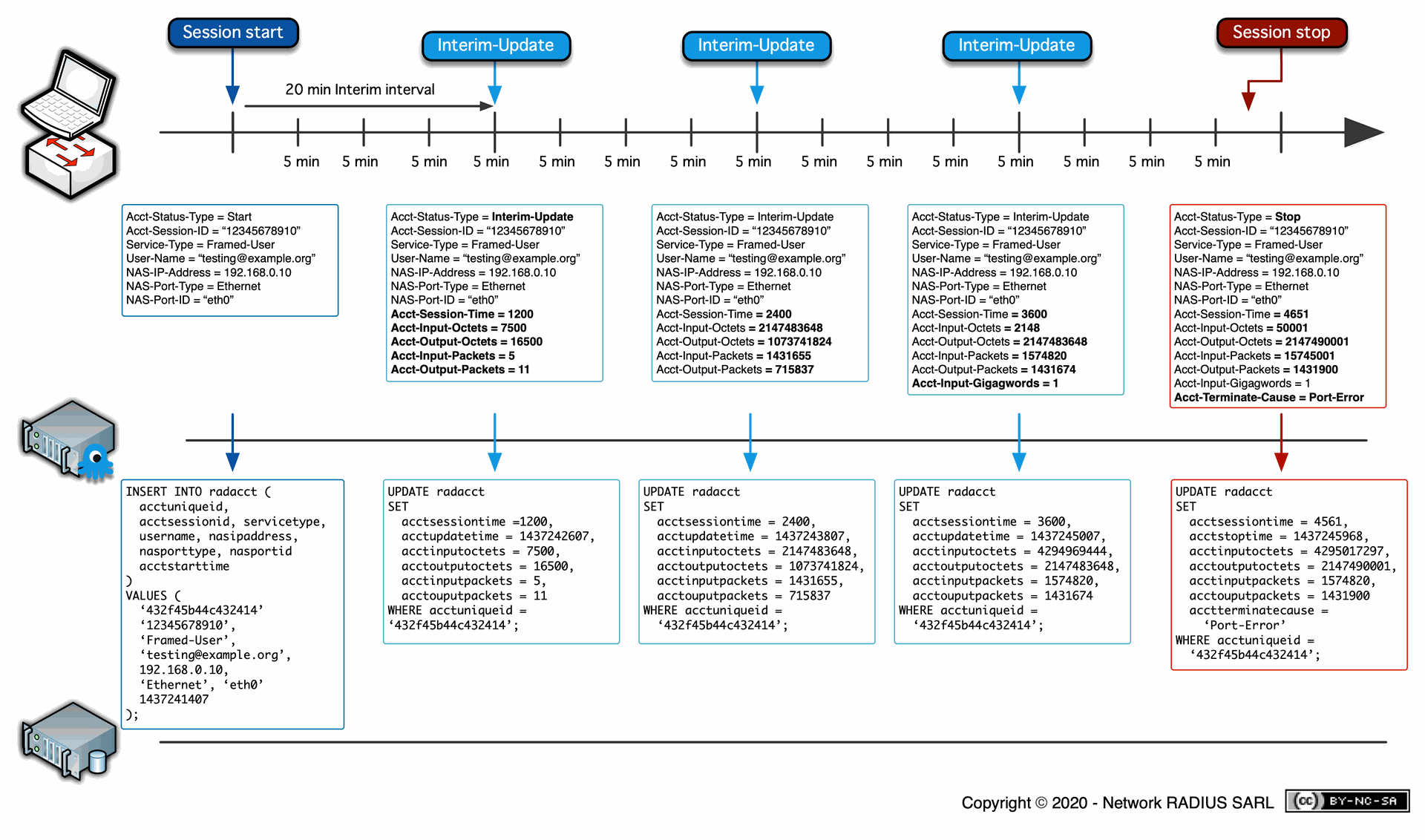
Step 2: Interim Updates
During the user's session, the NAS may send additional Accounting Request packets known as Interim Updates. These updates provide real-time information about the ongoing session, including:
- Current session duration
- Data usage and network traffic statistics
- Changes to network resources being accessed
- Any modifications to the user's permissions
These interim updates allow network administrators to monitor active sessions and track resource usage in real time, enhancing both the user experience and security through continuous monitoring.
The server can use these interim updates to check for total data usage and then send a Disconnect-Request packet if data usage is over a predefined limit.
Step 3: Accounting Stop
Once the user’s access to the RADIUS server has ceased, the NAS sends a final Accounting Request packet, known as an Accounting Stop record. This record provides comprehensive session information such as:
- Total session duration
- Complete data transfer volumes
- Packets transferred across types of network connections
- The specific reason for disconnection
- Any additional material relevant to the user's session
This detailed tracking ensures that internet service providers (ISPs) and organisations have complete visibility into how their network resources are being used.
The security benefits of RADIUS Accounting
RADIUS accounting works in conjunction with RADIUS authentication and authorisation to form a high-level security framework. While authentication verifies identities and authorisation controls access permissions, accounting provides the crucial audit trail that completes the security picture.
This accounting data allows organisations to:
- Monitor unusual patterns in network traffic
- Verify compliance with security policies
- Support forensic analysis after security incidents
- Provide data for complying with law enforcement requests about illegal activity by users (CALEA)
- Validate that authentication and authorisation controls are functioning properly
The system hosting your RADIUS solution can also generate comprehensive reports based on the accounting data, providing administrators with actionable intelligence about network security and usage patterns.
Accounting implementation considerations
When implementing RADIUS accounting, organisations should consider:
- Data Storage Requirements: Accounting records can grow quickly, especially in busy networks with many users.
- Privacy Considerations: Ensure your accounting implementation complies with relevant data protection regulations.
- Integration with Existing Systems: RADIUS accounting data should feed into your broader network monitoring and security infrastructure.
- Performance Impact: Configure accounting to balance between detail and system performance.
Need more help?
InkBridge Networks has been at the forefront of network security for over two decades, tackling complex challenges across various protocols and infrastructures. Our team of seasoned experts has encountered and solved nearly every conceivable network security issue. If you're looking for insights from the architects behind some of the internet's most foundational authentication systems, you can request a quote for network security solutions here.
Related Articles

Accounting: Keeping track of it all
We have already looked at authentication and authorization. In this third article, we’ll take a look at the accounting process, the process of monitoring and recording a client’s use of the network, and we’ll describe why it’s essential that the RADIUS server monitors user activity on the network.

Separating Authentication from your RADIUS Accounting server
Many ISP networks and enterprise environments handle both Authentication and Accounting functions through the same RADIUS servers and databases.